Introduction
In today’s digital age, where images play a crucial role in our personal and professional lives, ensuring the authenticity and integrity of these images has become a paramount concern. With the proliferation of advanced editing tools and the ease of sharing images online, the need for reliable image authentication software has never been greater. In this blog article, we will explore the concept of image authentication, its importance, and how it can be achieved using cutting-edge technology.
What is Image Authentication?
Image authentication refers to the process of verifying the integrity and origin of a digital image. It involves determining whether an image has been tampered with or manipulated in any way. By ensuring the authenticity of an image, we can trust its content and use it as reliable evidence in various domains, including forensic investigations, journalism, and digital media.
The Importance of Image Authentication
In today’s world, where fake news and manipulated images can spread like wildfire, the ability to authenticate images has become crucial. Image authentication software provides a robust solution to combat image tampering and manipulation, safeguarding the credibility and trustworthiness of digital images. Whether it’s detecting forged documents, identifying altered photographs, or ensuring the authenticity of evidence in legal proceedings, image authentication plays a vital role in maintaining integrity and transparency.
Cutting-Edge Technology: Image Authentication Software
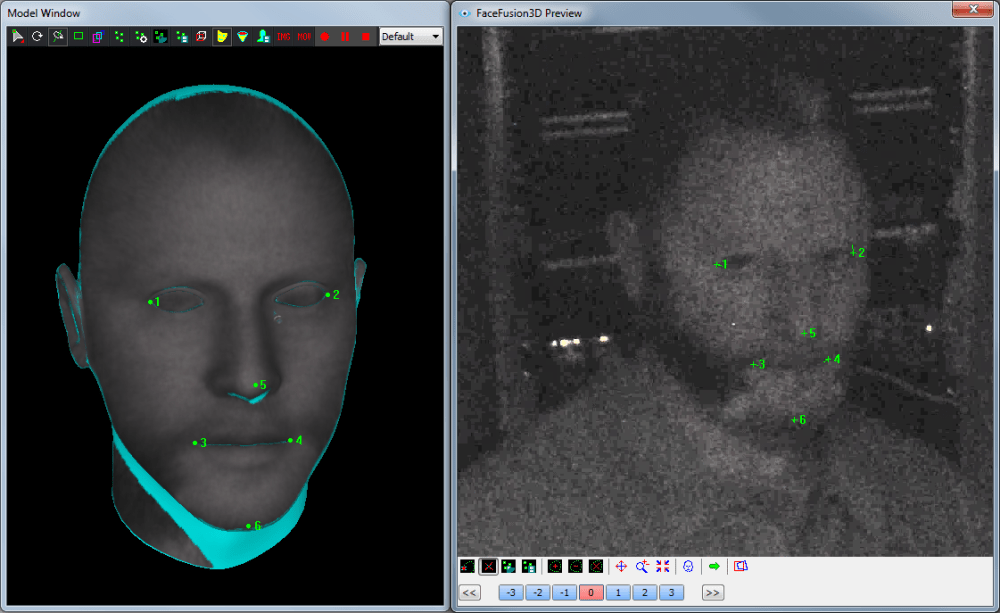
Thanks to advancements in technology, image authentication software has evolved to offer sophisticated and reliable methods for verifying the authenticity of digital images. One such software is offered by Cognitech, a leading provider of forensic image and video analysis solutions. Their image authentication software utilizes state-of-the-art algorithms and techniques to detect even the most subtle alterations in an image.
How Does Image Authentication Software Work?
Cognitech’s image authentication software employs advanced algorithms to analyze various aspects of an image, including pixel-level details, noise patterns, and metadata. By comparing these features with the original image data, the software can identify any discrepancies or modifications. The software also takes into account the camera sensor noise, lens aberrations, and other unique characteristics of the imaging device to establish the image’s authenticity.
Key Features of Cognitech’s Image Authentication Software
Cognitech’s image authentication software offers a range of powerful features that make it a reliable tool for verifying the integrity of digital images:
-
Pixel-level Analysis: The software meticulously analyzes the pixel-level details of an image to identify any alterations or manipulations.
-
Noise Pattern Analysis: By examining the noise patterns in an image, the software can detect inconsistencies that may indicate tampering.
-
Metadata Examination: Cognitech’s software extracts and analyzes metadata embedded in the image file, including camera make and model, GPS coordinates, and timestamps, to establish the image’s authenticity.
-
Forensic Comparison: The software allows for side-by-side comparison of multiple versions of an image, highlighting the differences and providing a comprehensive analysis.
-
User-Friendly Interface: Cognitech’s software boasts an intuitive and user-friendly interface, making it accessible to both forensic experts and non-technical users.
Conclusion
In an era where digital images have become an integral part of our lives, ensuring their authenticity and integrity is of utmost importance. Image authentication software, such as the one offered by Cognitech, provides a reliable and effective solution to combat image tampering and manipulation. By leveraging cutting-edge algorithms and techniques, this software allows us to verify the authenticity of digital images, maintaining transparency, and trust in various domains.